Research showed that the Locky Ransomware is now attacking users via social media in platforms like Facebook and LinkedIn.
People have become much more active regarding the protection of their personal information and digital security, because of all the hack methods that have happened on the web these past years. However, this forces the hackers to be more creative on how they will meddle in people’s devices.
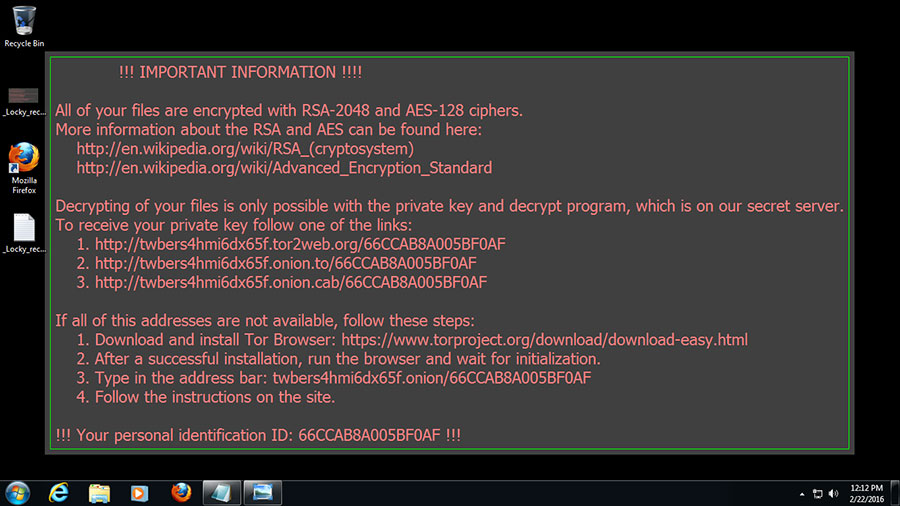
In the latest report made by the security company Check Point, the new mechanism that hackers are using is the propagation of malware in the image files that are on social platforms such as Facebook and LinkedIn, and maybe others in future days.
Experts said that this phenomenon occurring in social media is happening because of the lack of vigilance that security apps have on these sites.
Major social platforms like Facebook have well-functioning defense mechanisms (because of their big budgets) and doesn´t need the help of third party apps.
This causes that the people feel safer when downloading images from this kind of sites. But it seems that right now, this could be a bigger problem.
ImageGate
ImageGate is the new method hackers are using to embed malicious codes into existing files from social platforms. It could be in the form of extensions of SVG, HTA or JS and more commonly in JPG and PNG formats that are uploaded afterward.
The hackers modify the configuration of the social platform infrastructure to force users to download the images instead of just opening them in the website. Then, when the person clicks on the downloaded file image, the malware spread to the machine and locks out the user from their personal information.
The report from Check Point said that this is a new evolution of the Locky Ransomware method, in which the hackers ask for a specific amount of money for users to pay if they want their personal information back. Ars Technica has stated that the average amount that hackers demand is about half a bitcoin, $365.
Earlier this year, the digital company MalwareBytes performed a study regarding ‘Locky.’ They said that a significant amount of money is being invested in this project and that it seems to be maturing and improving in infrastructure. Back in July, they were the responsible for a digital attack done to a hospital in Kentucky, about the codification of medical data.
Locky has never used image files to perform their attacks, until now.
Facebook has declined and called incorrect both Ars Technica and Check Point studies. They, instead, blamed the Google Chromes extensions.
“This analysis is incorrect. There is no connection to Locky or any other ransomware, and this is not appearing on Messenger or Facebook. We investigated these reports and discovered there were several bad Chrome extensions, which we have been blocking for nearly a week. We also reported the bad browser extensions to the appropriate parties,” Facebook published in an official statement.
A Thrillist.com reporter contacted LinkedIn regarding this matter, and a spokesperson told the news agency that they believed this method was not very effective. However, LinkedIn assured their users that they are improving their security system in order to avoid any possible damage.
Microsoft Office also got damaged
Also earlier this year, ‘Locky’ conducted a series of hacking attacks trough Microsoft Office, more specifically by Microsoft Word. The user received an email that claimed the requirement for execution of a macro app within the Microsoft application. If you continue with the request, Locky could be installed in your computer and the malware will begin to spread.
According to a Palo Alto Networks report, this malicious organization was expecting to commit a “big hit” that involved the dissemination of the malware in over 400,000 devices.
How to avoid this malware
No matter if this hacking method comes from Facebook, LinkedIn or a Chrome Extension, the security measures are pretty much the same.
“If you have clicked on an image and your browser starts downloading a file, do not open it. Any social media website should display the picture without downloading any file. Don’t open any image file with unusual extension (such as SVG, JS or HTA),” has stated the security company Check Point about how to defend on this new hacking system.
Check Point recognizes that Locky knows how social media works and that all these websites are “whitelisted.” For this reason, users have to be careful about what files are opening and downloading, because it seems that this new method that consists of attacking social platforms and using them as delivery mechanisms are rising among hacking organizations.
In fact, Check Point has assured that this campaign from Locky is gaining strength and is getting more dangerous as more and more victims are reported across the globe.
Tech: Ars Technica
